| |
  |
|
E-CRYPTO |
|
|
E-Crypto are the first and only fully trustworthy solution for completely confidential mobile phone calls.
E-Crypto phones are
very easy to use and provide hassle-free, convenient security.They are
all based on the strongest encryption algorithms - AES 256 and Twofish.
Very long keys ensure the security of
your calls far into the future. E-Crypto products contain no backdoors
for anyone and can be fully verified by independent researchers.
E-Crypto phones offer worldwide
protection for your confidential phone calls, whether by GSM cellular
network (850, 900, 1800, 1900 Mhz), satellite or land line.
|
| |
 |
| |
|
| |
 |
E-Crypto G10i Quad Band
The E-Crypto G10i is a lightweight quad-band GSM mobile phone that comes with full source code available for independent review.
Secures your voice's privacy!
- Strongest and most secure algorithms available today
- AES256 and Twofish
- 4096 bit Diffie-Hellman key exchange with SHA256 hash function
- Readout-hash based key authentication
- 256 bit effective key length
- Encryption key is destroyed as soon as the call ends
- Source code available online for independent security assessments
- Also supports unencrypted calls, unencrypted SMS, address book, calendar etc.
- Works with any GSM 850/900/1800/1900 network that supports circuit-switched data calls
- Standby: up to 150 hours
- Talk time: Secure up to 5hours
- GPRS, OBEX, WLAN, Bluetooth, IrDa, USB, SD-card
- Dimensions: 98.5 x 51.4 x 15.8 mm
- Weight: 99 g incl. battery
|
| |
 |
| |
|
|
| |

Operational Features
Talk time up to 8 hours - standby time up to 270 hours
Dimensions & Weight
104.5 x 59 x 15.75 mm - 110g incl. battery - integrated antenna
Display
2.8-inch sunlight-readable transreflective TFT LCD screen with LED backlight @ 240x320, 64k colors
Navigation / Buttons
5-way navigation keypad - dedicated talk / hang-up buttons - volume up / down buttons
Connectivity
Integrated USB/ power/ audio connector
MicroSD memory card slot
Bluetooth V2.0 with Enhanced Data Rate and A2DP for stereo wireless headsets
IEEE 802.11 b/g Wireless LAN
Audio codecs
Encrypted calls: CELP and ACELP® VLBR4
Decoding & playback: WAV, WMA, AMR-NB, AMR-WB, AAC, AAC+, eAAC+, QCP, MP3, polyphonic ring tones
CMOS Camera
2.0 megapixels resolution (can be completely disabled upon request)
Standard Accessories
100-240V AC adapter - USB sync cable - tereo headset with microphone
|
E-Crypto 301
Secure GSM Phone with Voice & SMS Encryption
TECHNICAL SPECIFICATIONS
Radio
GSM quad-band 850/900/1800/1900MHz
EDGE EGPRS class B, multi-slot class 10
CSD
Voice Encryption
Strongest and most secure algorithms available today AES256 and Twofish
4096 bit Diffie-Hellman key exchange with SHA256 hash function
readout-hash based key authentication
256 bit effective key length
encryption key is destroyed as soon as the call ends
Message Encryption
Based on the same strong encryption algorithms used for E-Crypto voice encryption - 4096 bit Diffie-Hellman initial key exchange, AES256 and Twofish message encryption with 256 bit effective key length. Supports long SMS and encrypted self-destructing "Eyes Only" SMS.
Device Protection
Encrypted storage system for contacts, messages, notes and keys with smart folders protects confidential data against unauthorized access
hardened WM 6.1 operating system with granular security management and streamlined, security-optimized components and communication stacks protects device against outside attacks
E-Crypto phones are the only secure mobile phones on the market with full source code published for independent security assessments. They contain no »proprietary« or »secret« encryption, no backdoors, no key-escrow, no centralized or operator-owned key generation, and require no key registration.
Interoperability
Fully compatible with all E-Crypto phones circuit-switched mobile, satellite and fixed-line encryption products
PBX integration available
Trustworthy Voice & SMS Encryption
The E-Crypto 301 comes with full source code available for independent review. Finally, you can perform an independent assessment to ensure that you can rely on strong encryption without any backdoors in the communications device that you entrust your security to. The E-Crypto 301 enables you to put the trust where it belongs in a trustworthy, open and scientific verification process.
E-Crypto technology is based on well-researched algorithms for both encryption and voice processing. It features the strongest encryption available combined with key lengths that provide peace of mind today and in the future.
Optional Accessories
12V car
charger - solar panel charger - vehicle mount kit
Satellite
Upgrade Option
Upgradeable to dual-mode secure GSM and Thuraya
satellite communications using the E-Crypto T2 upgrade package
|
| |
|
| |
Operational Features
Talk time up to 5 hours
standby time up to 360 hours
Dimensions & weight
107.9 x 53.1 x 13.7 mm
118g incl. battery
integrated antenna
Display
3.2-inch sunlight-readable touch-sensitive TFT LCD
screen with LED backlight @ 480 x 800, 64k colors
Navigation / Buttons
Dedicated talk / hang-up, volume up / down, home and back buttons
touch-activated zoom bar
Connectivity
Integrated USB/ power/ audio connector
MicroSD memory card slot, SD2.0 compatible
Bluetooth
V2.0 with Enhanced Data Rate and A2DP for stereo wireless headsets
GPS
IEEE 802.11 b/g Wireless LAN
Audio Codecs
Encrypted calls: CELP and ACELP® VLBR4
Decoding & playback: WAV, WMA, AMR-NB, AMR-WB, AAC, AAC+, eAAC+, QCP, M4A, MP3, MIDI, polyphonic ring tones
CMOS Camera
5.0 megapixels resolution with auto focus (can be completely disabled upon request)
Standard Accessories
100-240V AC adapter
USB sync cable
stereo headset with microphone
Optional Accessories
12V car charger
solar panel charger
vehicle mount kit
|
E-Crypto 400
Secure IP Mobile Phone with Voice & SMS EncryptionSecure IP Mobile Phone with Voice & SMS Encryption
The E-Crypto 400 is a secure IP mobile phone for secure voice over IP communication on any network GSM, 3G or WLAN.
The E-Crypto 400 gives you the flexibility to conduct secure voice over IP calls using either GSM, 3G/UMTS, or wireless local area networks. This unmatched flexibility combined with secure messaging, a hardened operating system and encrypted storage for your confidential contacts, messages and notes provides you with 360-degree protection in a sleek, elegant package including a brillant 3.2-inch TFT LCD high-resolution touch screen.
- Quad-band GSM
- Dual-band UMTS / 3G
- Wireless LAN
- Voice & SMS encryption
- Secure storage
- Hardened operating system
- Standby: Up to 360 hours
- Secure talk time: Up to 5 hours
TECHNICAL SPECIFICATIONS
Radio
-
GSM quad-band 850/900/1800/1900 MHz
-
UMTS HSDPA/WCDMA 900/2100 MHz with HSUPA support
-
Up to 2 Mbps uplink, up to 7 Mbps downlink speed
Voice Encryption
-
Secure voice over IP communication on any network GSM, 3G, WLAN
-
strongest and most secure algorithms available today AES256 and Twofish
-
4096 bit Diffie-Hellman key exchange with SHA256 hash function
-
readout-hash based key authentication
-
256 bit effective key length
-
encryption key is destroyed as soon as the call end
Message Encryption
-
Based on the same strong encryption algorithms used for E-Crypto phone voice encryption
-
4096 bit Diffie-Hellman initial key exchange, AES256 and Twofish message encryption with
-
256 bit effective key length. Supports long SMS and encrypted self-destructing "Eyes Only" SMS.
Device Protection
Encrypted storage system for contacts, messages, notes and keys with smart folders protects confidential data against unauthorized access hardened WM 6.5 operating system with granular security management and streamlined, security-
optimized components and communication stacks protects device against outside attacks
E-Crypto phones are the only secure mobile phones on the market with full source code published for independent security assessments.
They contain no »proprietary« or »secret« encryption, no backdoors, no key-escrow, no centralized or operator-owned key generation, and require no key registration.
Interoperability
Fully compatible with all E-Crypto IP mobile, satellite and fixed-line encryption products
IP PBX integration with virtual extensions
Trustworthy Voice & SMS Encryption
The E-Crypto 400 comes with full source code available for independent review. Finally, you can perform an independent assessment to ensure that you can rely on strong encryption without any backdoors in the communications device that you entrust your security to.
The E-Crypto 400 enables you to put the trust where it belongs in a trustworthy, open and scientific verification process.
E-Crypto technology is based on well-researched algorithms for both encryption and voice processing. It features the strongest encryption available combined with key lengths that provide peace of mind today and in the future
|
| |
|
|
| |

Operational Features
-
LED call indication
-
programmable secure phonebook
-
redial function
-
ringer and hand-set volume control
-
mute function
-
DND (do encryption available combined with key lengths not disturb) mode that provide peace of mind today and in the future.
Dimensions & Weight
-
230 x 200 x 30 mm / 9.1 x 7.9 x 1.2 in.,
-
690g / 1.5lbs without footstand (920g / 2.1lbs with footstand)
-
black or light gray color scheme
Display
-
4.3-inch sunlight-readable touch-sensitive TFT LCD
-
screen with LED backlight @ 480 x 272, 16.7mn colors
Connectivity
-
RJ-4P4C headset connector
-
optional 2x USB Type A connectors for special communications equipment
Power
-
IEEE 802.3ad, Class 1 Power over Ethernet or AC power 100 to 240 VAC, 50-60 Hz, 7 watts maximum operating power
EMI/EMC & Safety Approvals
-
FCC Part 15 Subpart B Class B, CE
-
IEC60950-1:2001
Standard Accessories
-
100-240V AC power adapter
-
full cable set
Optional Accessories
-
100-240V AC uninterruptible power supply
-
solar panel power pack
-
headset with background noise suppression
|
E-Crypto IP19
The E-Crypto IP19 phone is a secure IP desktop phone for end-to-end encrypted voice over IP communications on any IP network.
The E-Crypto IP19 features a Gigabit Ethernet interface with an R45 plug, and optional support for wireless LAN. It uses the same encryption engine as E-Crypto's secure mobile and satellite phones, featuring 256-bit AES and Twofish session encryption and a 4096-bit Diffie-Hellman key exchange, readout-hash based key authentication, and session keys that are newly generated for each call and destroyed after the call ends.
The E-Crypto IP19 is easy to use and easy to set up, using a large color touch screen display. Fully compatible with E-Crypto IP mobile and satellite phones, it offers the latest technology for reliable and secure end-to-end encrypted voice over IP communications.
- End-to-end IP voice encryption
- Easy to use, easy to install
- Compatible with Inmarsat BGAN, Thuraya IP, VSAT satellite terminals
TECHNICAL SPECIFICATIONS
Telephone IP Network Interface
-
Gigabit Ethernet IEEE 802.3 10/100/1000 BaseT with RJ45 plug
-
Compatible with Inmarsat BGAN satellite terminals
-
Optional IEEE 802.11b/g/n wireless LAN support
Voice Encryption
-
Secure voice over IP communication on any IP network
-
strongest and most secure algorithms available today - AES256 and Twofish
-
4096 bit Diffie-Hellman key exchange with SHA256 hash function
-
readout-hash based key authentication
-
256 bit effective key length
-
encryption key is destroyed as soon as the call ends
Device Protection
-
Encrypted storage system for contacts protects confidential data against unauthorized access
-
hardened Linux operating system with security-optimized components and communication stacks protects device against outside attacks.
-
E-Crypto phones are the only secure phones on the market with full source code available for independent security assessments. They contain no »proprietary« or »secret« encryption, no backdoors, no key-escrow, no centralized or Trustworthy Voice Encryption operator-owned key generation, and require no key registration.
Interoperability
-
Fully compatible with all E-Crypto IP mobile, satellite and fixed-line encryption products IP PBX integration with virtual extensions.
Operational Features
LED call indication programmable secure phonebook redial function ringer and handset volume control mute function DND mode (do not disturb).
Trustworthy Voice & SMS Encryption
-
The E-Crypto IP19 comes with full source code available for independent review. Finally, you can perform an independent assessment to ensure that you can rely on strong encryption without any backdoors in the communications device that you entrust your security to.
-
The E-Crypto IP19 enables you to put the trust where it belongs in a trustworthy, open and scientific verification process.
-
E-Crypto technology is based on well-researched algorithms for both encryption and voice processing. It features the strongest encryption available combined with key lengths that provide peace of mind today and in the future.
|
| |
|
|
| |
|
See also YES ONE and YES TWO Free Roaming SIM
|
| |
 |
| |

|
E-Crypto PSTN/1i
The PSTN/1 is a secure desktop phone
that connects to the public switched telephone network and comes with
full source code available for independent review. Secures your voice's privacy !
- Strongest and most secure algorithms available today
- AES256 and Twofish
- 4096 bit Diffie-Hellman key exchange with SHA256 hash function
- Readout-hash based key authentication
- 256 bit effective key length
- Encryption key is destroyed as soon as the call ends
- Source code available online for independent security assessments
- Standard analog PSTN/POTS interface with RJ11/RJ13 plug
- Audio port for interfacing the PSTN/1 with video conferencing equipment
- Integrated interface for connection to Inmarsat , Iridium or Thuraya satellite terminals
- One Touch switch for encrypted / non encrypted calls
- Dimensions: 50 x 275 x 172mm (Encryption Unit)
- Weight: 2200g
|
| |
|
|
| |
  |
E-Crypto T3 Thuraya Satellite Option
The T2 Thuraya satellite option is
the perfect solution for secure communications in areas without GSM
coverage or if you do not with to depend on local network infrastructure.
Secure Thuraya satellite communication option for all E-Crypto mobile phones.
Secure
satellite communication utilizing the crypto engine with the strongest
and most secure algorithms available today - AES256 and Twofish.
4096 bit Diffie-Hellman key exchange with SHA256 hash function
Readout-hash based key authentication
256 bit effective key length
Encryption key is destroyed assoon as the call ends
Source code available online for independent security assessments
Consists of wireless docking station for Thuraya satellite terminal and firmware upgrade for all current E-Crypto mobile phones
Talk time: Supports up
to 8 hours of encrypted Thuraya satellite calls (depending on usage
patterns) with any E-Crypto mobile phone.
|
| |
|
|
| |
 |
E-Crypto for Windows - WIN
Free software for land lines.
Runs on any modern desktop or notebook computer running under Microsoft Windows(TM)
Allows for easy and secure communication to and from mobile E-Crypto products as well as to other E-Crypto for Windows users
Requires
supported modem on POTS or ISDN landline (Galaxy MU32S, Modems with the
Cirrus-Chipset"CL14xx", ELSA microlink 28.8TQV (testing reference),
US-Robotics56000 courier) or one of the following GSM modems: Nokia
9210 or Siemens S35/M35/C35
Sorry; the E-Crypto for Windows Application does not work with Winmodems at this time.
Our E-Crypto customers have access to this download in our secure customer support area.
|
| |
|
|
| |
 |
E-Crypto ISDN and VOIP Gateway
The E-Crypto Gateway for ISDN and Voice over IP (VoIP) private branch exchanges is fully compatible with all E-Crypto secure mobile phones.
|
| |
|
See also YES ONE and YES TWO Free Roaming SIM
|
| |
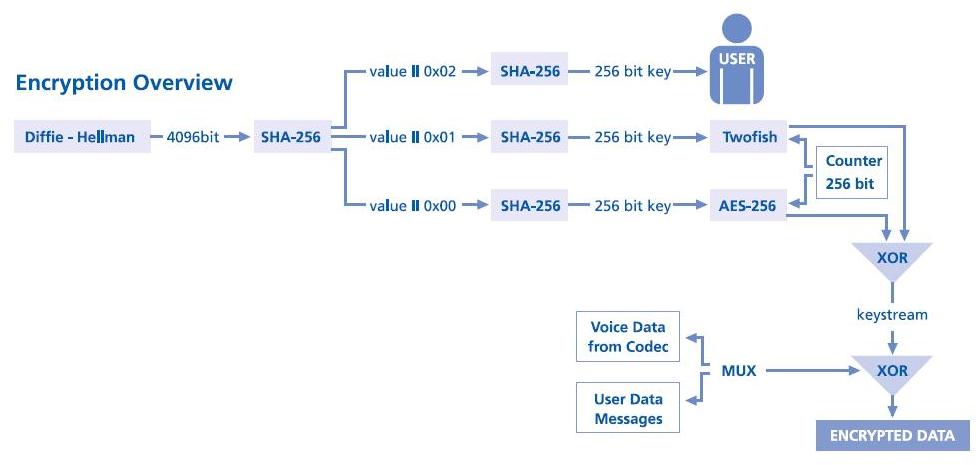
What kind of cryptography and what key length is used in the E-Crypto?
All calls are encrypted with 256-bit keys using AES and Twofish as
counter mode stream ciphers. Using both AES and Twofish results in much
stronger encryption than using only one algorithm. For the highly unlikely case
that a weakness is discovered in one of the algorithms, the use of the second
algorithm provides still a sufficient margin of security. The use of the two
very strong algorithms is a unique feature of the E-Crypto. The key used is
generated using a 4096-bit Diffie-Hellman shared secret exchange.
The crypto block diagram is shown below.
What is the voice compression used in the E-Crypto? How does it sound?
Is there a delay?
The basic design of a secure GSM phone is to take the voice from the
microphone, digitize it and run it through a compression algorithm, before
encrypting it and sending it via a GSM data call to the other party. The
compression algorithm is also called a codec and does with voice what mp3 does
with music - making sure it takes up less data.
E-Crypto use the CELP Codec running at 8kHz. The output stream of the
codec is 4.8kbit/second, enabling it to be transported over a 9,6kbit GSM data
call.
The speech and sound quality you can expect is comparable to
transcontinental phone calls. You should note that the overall speech quality
depends on the GSM signal quality, so degradation does happen in low coverage
areas. While in unencrypted GSM the sound quality gets bad and you would
experience dropouts as the phone moves out of coverage, with the E-Crypto under
the same circumstances the call delay would increase. Simple indicators on the
E-Crypto show GSM signal coverage and call quality / delay.
All calls made with the E-Crypto are subject to a certain delay in the
call, as if your call is routed over a satellite link. Most of the call delay
originates from the way GSM networks handle the data calls. The E-Crypto must
use the GSM data call instead of the normal voice call mode to ensure a
transparent communications channel between the two E-Crypto. Because the delay
is a side-effect of all GSM data calls there is nothing we can do about it. All
available GSM encryption products on the market suffer equally from this delay.
The E-Crypto itself introduces comparatively little delay from the voice
encoding and encryption.
|
|

|
| |
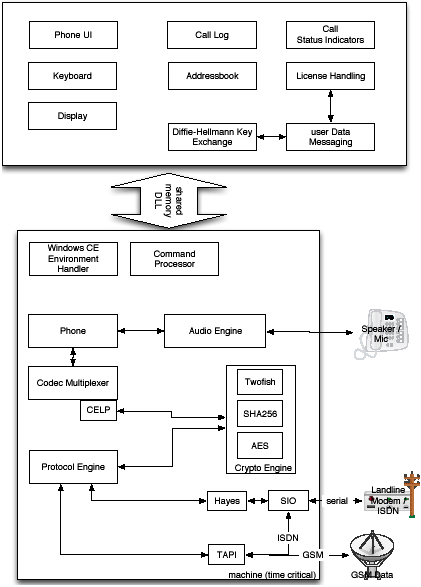
So
what does the software architecture of the E-Crypto look like? |
| |
 |
| |
|
|
| |
|
| |
top
|
Contact us now for your E-Crypto here ...
|
|
|
|
|
|
















